DATA EXTRACTION PLATFORM
Data-extraction solution that is truly secure.
A new platform purpose built for Internet connected endpoints because just focusing on ETL functions is not enough
Data-stream security
Secure extraction, transformation and transmission using military grade labeling, binding and encryption procedures.
Vendor independence
Eliminate data-silos! Add data-sources and destinations, while maintaining unified data-stores.
Location independence
Remote, Local, Legacy, Digital, on-premise or in the cloud – securely extract data regardless of location.
Data-as-a-Service
A global data-routing network to efficiently & securely route data from sources to destinations.
Data control
Real time data streamed to you. Own, maintain and govern your data sovereignty and compliance.
Pay-as-you-grow
Start small and grow as you transform your organizational data footprint.


Data-stream security
Secure extraction, transformation and transmission using military grade labeling, binding and encryption procedures.

Data-as-a-Service
A global data-routing network to efficiently & securely route data from sources to destinations.

Data control
Real time data streamed to you. Own, maintain and govern your data sovereignty and compliance.

Pay-as-you-grow
Start small and grow as you transform your organizational data footprint.

Location independence
Remote, Local, Legacy, Digital, on-premise or in the cloud – securely extract data regardless of location.

Vendor independence
Eliminate data-silos! Add data-sources and destinations, while maintaining unified data-stores.
Pay-as-you-grow
Start small and grow as you transform your organizational data footprint.
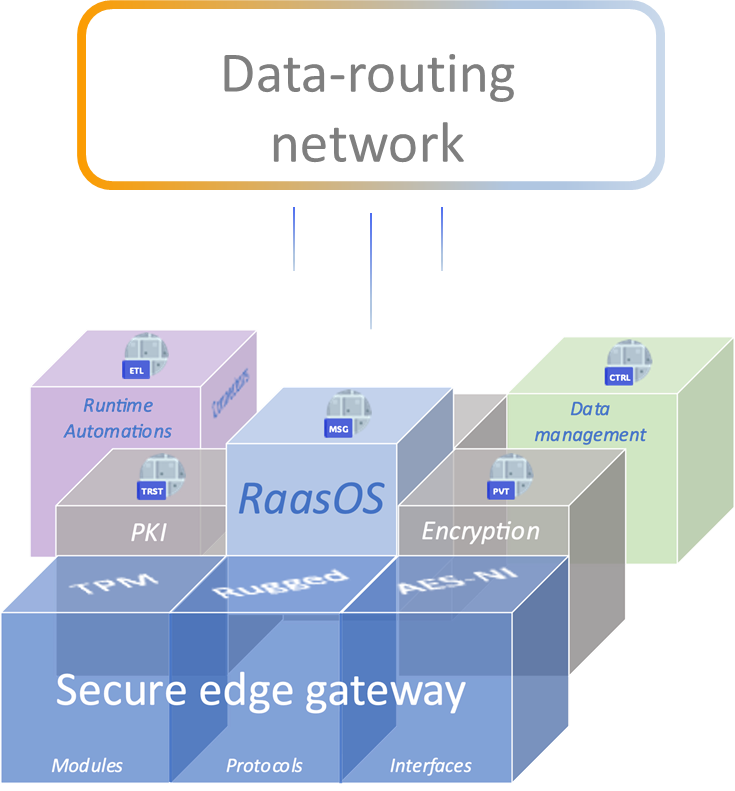
FROM SOFTWARE ONLY TO HARDWARE-ASSISTED SECURITY
Embed security in every stage starting at the edge
A range of pre-packaged deployment specific hardware and software edges, offering a comprehensive and flexible security-hardened zero-touch deployment solutions for locations where security matters the most.

Protected ETL
Data processing functions designed for remote executions.

Secure messaging
Mutually authenticated & encrypted connections to a global data routing network.

Metadata labelling & binding
Military grade confidentiality management framework.

Secure Edge
Hardware assisted security and operations.

Zero Trust services
Embedded resource controls & cyber protection.

Encryption services
Data encryption both at rest and in transit.
FROM DATA-STORAGE TO DATA-STREAMING
Own your data using DataStream-as-a-Service
Data-aggregation solutions collect and store your data in their clouds. Doing so, does not only raise concerns about data-security and sovereignty, but could also result in ever increasing data storage and access fees. Charging you to get access to your own data – really? – yeh – I know!
Raasify’s global data-as-a-service routing infrastructure delivers powerful virtual private communication services all the way to the edge, securely and reliably connecting, segmenting, prioritizing, routing, replicating and efficiently aggregating encrypted data-streams from sources to destinations. The extended data-routing-fabric ensures that data-sources and destinations are never exposed to the Internet, remaining private and protected from cybersecurity threats and data-theft. The global data-routing network is a transactional streaming platform, delivering your data-streams to you in real-time.

FROM UNPROTECTED ETL TO SECURE DATA-STREAMING
Protected ETL functions keep your data safe

Existing data Extraction, Transformation and Loading (ETL) solutions focus on data manipulation, often failing to consider data-security. Encrypting data in-transit is often insufficient to ensure that data is protected. The environment which these functions are performed and how data is protected prior, during and post such operations must also be considered.
Raasify secure edge gateways deliver Protected ETL functionality – a new level of security for data-extraction. Each secure edge gateway creates a secure and private runtime environment for executing ETL functions. Data is extracted, transformed and encrypted both at rest and as it is transmitted across the Raasify secure data-routing network towards its destinations.
FROM TRUST TO VERIFY
Don’t trust! Enforce data security.
Often data security is equated with data encryption. Although encryption is a good first step, it may ensure privacy but not security.
As part of a wholistic approach to information management, Raasify’s data extraction platform binds data objects with confidentiality metadata labels to deliver unprecedented data classification, traceability, integrity and authenticity to enforce data security at every stage of data-extraction – so you can trust your data!

Introducing Our
Amazing features
Next-generation software architecture designed Internet based communication in the cloud-era.
Cloud-based
- Create automations that are infrastructure agnostic, automating any endpoint right from your browser
- Unify disparate interfaces to a centralized API across all endpoints and applications
- Scale your operations on-demand to meet your business needs as your business grows
- Control your budgets and pay as you go to align savings with value based on a subscription pay-as-you-go model

Secure
- Segment automations to a single deployment or across your business depending on endpoint type, security level and/or geography
- Control access based on identity and zero-trust to restrict automations to permitted applications and/or users.
- Integrate your existing identity management systems to seamlessly align with your business existing access policies
- Centralize your automations into unified and fully auditable repositories, doing away with untraceable files, inconsistent configurations and unsecure directories.
Low-code
- Minimize the need for specialized technical skills using simple dragand-drop editors and workflow components.
- Cultivate hyper-automation practices through the collaboration of technical and non-technical and cross-departmental personnel.
- Improve repeatability through template-based human-readable automation workflows that minimize rework and duplication
- Reduce the impact of new technology introduction using abstracted vendor-independent automations that to deliver plug-and-play operations


Location-less
- Achieve plug and play operations using raasify’s software agents or dedicated appliances to meet location deployment requirements
- Integrate with existing deployments and infrastructure with no changes to existing business and IT systems
- Unify on-premise and cloud applications management practices as part of your hybrid-IT and multi-cloud strategies
Collaborative
- Implement centralized repositories for all your business automations that are accessible from anywhere
- Create automation marketplace packages that are private or public to maximize reuse, minimizing rework and monetize your intellectual property
- Invite your peers, employees, partners and suppliers to collaborate to drive innovation throughout your organization

OUR TECHNOLOGY INTEGRATIONS

Streamlined processes for collecting data to power your Organization
RAAS Steps
Get a Better look
- Step 1: Register your organization using raasify’s self-registration portal
- Step 2: Activate locations using raasify’s plug-and-play deployment model
- Step 3: Aggregate your data using raasify’s automation marketplace packages
- Step 4: Scale on-demand to meet your organizational needs